Lupine Publishers | Journal of Anesthesia & Pain Medicine
Abstract
Introduction: the physiological response to the aggression produced by the surgical trauma provides the effective treatment capacity in case of complications. Surgical intervention causes endocrine, metabolic, autonomic, immunological, and hematological changes.
Objective: to estimate the predictive factors of the second window of myocardial ischemic preconditioning in the patients proposed for elective surgical interventions.
Material and Methods: A quasi-experimental study was carried out in the period January to December 2019 at the Maria Curie Cancer Hospital in Camagüey with patients who met inclusion and exclusion criteria in preoperative consultation in the research period, to whom preconditioning was applied. Ischemic two hours before surgery. Chi squared and logistic regression was calculated as appropriate.
Results: Predictive factors such as essential arterial hypertension odds ratio 16,632, diabetes mellitus 12,157, age 60 years and over with odds ratios of 8,035, heart failure odds ratio 6,433, cerebrovascular disease odds ratio 6,135, and chronic kidney disease were estimated. Odds ratio 5,800 and chronic obstructive pulmonary disease with odds ratio 5,738.
Conclusion: the predictive factors of the second window of ischemic preconditioning were independent predictors of risk in elective surgical patients.
Keywords:Preconditioning; Elective surgical patient; Surgical stress; Predictive factors
Introduction
Knowledge of the physiological response to aggression produced by surgical trauma provides effective treatment capacity in the event of complications. Surgical intervention causes endocrine, metabolic, autonomic, immunological, and hematologic changes [1]. Somatic and autonomic afferent nerve impulses generated at the site of injury activate the endocrine response, while the inflammatory and immune response, mediated by hormones, begins to develop. and cytokines, secreted products of activated leukocytes, fibroblasts, and endothelial cells. The changes in the immune and endocrine systems in the face of surgical trauma, are objectified by the perioperative response of various markers. Surgical stress is a situation in which there is both an increase in the speed of generation of oxidizing species, free radicals (RL) and excited species, and a decrease in the activity of defense systems, resulting in higher concentrations, in the steady state of active oxygen species [2,3]. In these situations, the toxic effects of these RLs manifest and chemical reactions take place on lipids, proteins and carbohydrates inside the cells, which trigger irreversible damage and even death cellular. There are numerous diseases associated with the imbalance between oxidants and antioxidants, in the surgical patient from the preoperative period with personal pathological history, he becomes involved with the RL, through the physiological response of the diseases and the complexity of the surgical trauma as essential factors in the perioperative changes of hemostasis, the interaction of the endocrine and immune axis and of the drugs administered in the surgical anesthetic act [4]. The publication that describes the influence of anesthetics used during the perioperative period and the typical hormonal response generated by the surgical intervention and the patient is current. With modulation of adrenal response by the distribution of leukocytes and their immune functions. Anesthetics modify immune function by reducing the stress response and have a direct effect on immune cells [5]. The investigation was carried out with the objective of estimating the predictive factors of the second window of myocardial ischemic preconditioning in surgical patient’s elective for myocardial protection during major surgical intervention.
Material and Methods
General Aspects of the Study
This was a quasi-experimental investigation to estimate the predictive factors of the second window of myocardial ischemic preconditioning in elective surgical patients at the María Curie Cancer Hospital in Camagüey in the period from January to December 2019.
Definition of the Study Universe
The study population was delimited to 40 preconditioned patients 2 hours before the surgical intervention, an insufflated sphygmomanometer was placed at 200 mmHg for 5 minutes, after this time it is deflated, and 5 minutes are expected. This procedure is repeated 3 times. Blood draws are performed before and after the application of ischemic preconditioning. They are preconditioned and post conditioned patients who meet the inclusion and exclusion criteria.
Inclusion Criteria
Patients aged 20 years and over proposed for major elective surgical intervention.
Exclusion Criteria
Patients who do not offer their consent to participate in the research. Variables: age, sex, associated risk factors, antioxidant markers, discharge status, hospital stay, complications. The antioxidant markers before and after the preconditioning were determined: the concentration of reduced glutathione (GSH) by the method of Sedlak et al. [6] and malonic aldehyde (MAD).
Information Processing and Analysis Plan
Search and collection of information: A form was completed for each patient, complementing the information with data from the medical records.
Information processing: The database was compiled with the collected information, which was processed automatically using the SPSS statistical package. The information of the qualitative variables is summarized in descriptive statistics, related to the characterization of the patients operated on by the different surgical specialties, to determine the behavior of the activity of antioxidant and oxidant markers (preconditioning and postconditioning). The information resulting from applying the second window of ischemic preconditioning was processed according to the univariate and multivariate analysis for the study variables using the statistical program SPSS version 21. Implementing the chi-square test and logistic regression as appropriate. The understanding of the results obtained is facilitated through statistical tables and graphs, it was analyzed giving an answer to each proposed objective and comparing the results with those of other authors. Finally, after a synthesis work, conclusions and recommendations were issued [7].
Results and Discussion
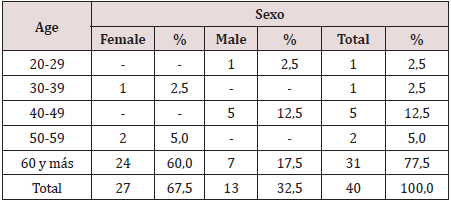
N 40 Source: clinical history as can be seen in Table 1, most of the surgical oncology patients belong to the group of 60 years and more, for 77.5%. The evolution of the age pyramid, thanks to the increase in life expectancy and better healthcare, places cancer diseases in the forefront of surgery, influenced by the life expectancy at birth of 80.2 years for women and 76 years for the men. Cuba is among the three countries on the continent with the largest aging population, in 2000 it exceeded 1.6 million older adults and in 2014 it represented 17.9% of the total population, in 2015 the Cuban population was 18.5% and in 2018 21% of the population aged 60 and over 6.7 During the aging process, the adult heart undergoes numerous biochemical, ultrastructural, functional and anatomical changes that reshape cell structure, function and adaptive responses to stress. Histologically, a decrease in the number of myocytes and progressive hypertrophy of these are observed in both ventricles. Also, studies in humans demonstrated aging-related abnormalities in cardiac metabolism, coronary flow reserve, endothelial function. Age is an independent predictor of risk in patients with coronary heart disease, this is explained by the lack of adaptation to acute myocardial ischemia [8]. Ischemic preconditioning is a mechanism by which repetitive episodes of ischemia induce greater tolerance in the myocardium to subsequent episodes of aging as a biological process with interindividual variability leading to the progressive loss of physiological functional reserve, the alteration of these functions is not evident. in basal situation but it manifests itself in moments of stress such as illness and perioperative.
Table 2: Frequency distribution of patients with ischemic preconditioning according to personal pathological history.
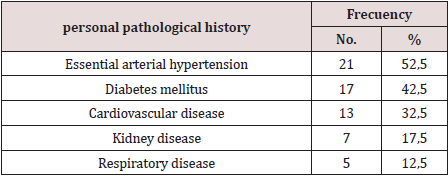
N 40 Source: clinical history
In Table 2, twenty-one patients out of forty preconditioned have a diagnosis of essential arterial hypertension with 52.5% followed by diabetes mellitus 42.5% and cardiovascular disease 32.5%. Comorbidity is more frequent and both cerebrovascular disease and lung processes, kidney failure, hypertension, and diabetes justify part of the increased risk of the surgical patient. However, it seems useful to recall other pathophysiological mechanisms that explain the elderly’s reduced response capacity such as endothelial dysfunction, microcirculatory disorders (rarefaction), increased precapillary resistance, and decreased ability to develop collateral circulation as clear. Limiting residual flow in the risk area and perfusion flow in the remote area [9,10]. In the myocardium, the possible loss of ischemic preconditioning, the accelerated drop in the reserve of high-energy phosphates (lower tolerance to ischemia), calcium overload and senile myomalacia are factors to consider. The primary changes of arterial aging produce important secondary changes in the heart and other terminal organs, including the brain and kidneys. The vascular aging process is accelerated by the presence of primary cardiovascular disease, including high blood pressure and atherosclerosis, as well as by other risk factors such as diabetes, smoking, and obesity. Morphological changes include a decrease in the number of myocytes, a thickening of the left ventricular wall, and a decrease in both the density of the conduction fibers and the number of cells in the sinus nodes [11]. These changes are readily apparent in terms of elevated mean arterial pressure and increased pulse pressure. Increased vascular stiffness leads to significant secondary cardiac responses, but in young people the heart pump and blood vessels are optimally coupled for maximum efficacy. The mere fact of treating the topic of aging and optimizing the preoperative period of the surgical patient with the application of preconditioning due to ischemia is the objective of the research Table 3.
Table 3: Frequency distribution of patients with ischemic preconditioning according to personal pathological history.
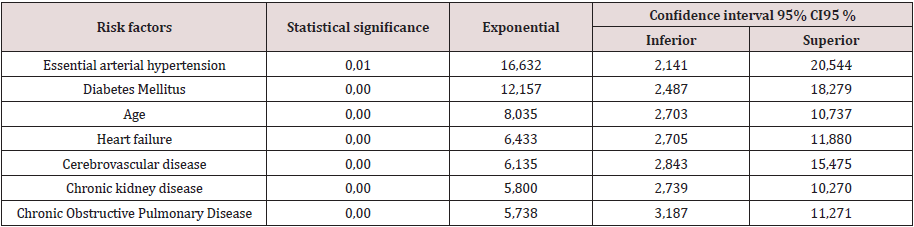
N 40 Source: clinical history
Interpreting the adjusted odds ratio (OR) for the variables of the
equation as follows: In the estimated Logistic Regression function,
the variable essential arterial hypertension had a significantly
different regression coefficient of 0 (p = 0.01) and adjusted OR
of 16,632 (95% CI 2,141; 20.54). In this analysis, the risk of not
modulating (oxidative enzymatic response) is approximately 7
times greater in patients with positive oxidative stress markers
than in negative ones, that is, the enzymatic response after
preconditioning is at the expense of oxidants. The diabetes mellitus
variable had a significantly different regression coefficient of 0 (p
= 0.00) and adjusted OR of 12,157 (95% CI 2.487; 18.279), which
implies that the risk of presenting enzymatic response to diabetes
mellitus patients Oxidant expense is approximately 12 times
greater than in those without a history of diabetes mellitus.
A patient 60 years and older after ischemic preconditioning
is 8 times more likely to have an oxidative enzymatic response
with OR (8,035) and 95% CI 2,703; 10,737. The variable Heart
failure had a regression coefficient other than 0 (p = 0.00) and adjusted OR 6,433 (95% CI 2,705; 11,880), which implies the
risk of presenting the oxidative enzymatic response in patients
with a history of heart failure. After ischemic preconditioning, it
is 6 times higher than in patients without a personal pathological
history of heart failure, with a margin of 2 to 11 times. The variable
cerebrovascular disease had a regression coefficient other than 0
(p = 0.00) and adjusted OR 6,135 (95% CI 2,843; 15,475), which
implies the risk of presenting the oxidative enzymatic response in
patients with a history of cerebrovascular disease. After ischemic
preconditioning, it is 6 times greater than in patients without a
personal pathological history of cerebrovascular disease, with a
margin of 2 to 15 times. The variable chronic kidney disease had a
regression coefficient other than 0 (p = 0.00) and adjusted OR 5,800
(95% CI 2,739; 10,270), which implies the risk of presenting the
oxidative enzymatic response in patients with a history of disease.
Chronic renal disease after ischemic preconditioning is 5 times
higher than in patients without a personal pathological history
of cerebrovascular disease with a margin of 2 to 10 times. The
variable chronic obstructive pulmonary disease had a regression
coefficient other than 0 (p = 0.00) and adjusted OR of 5,738 (95%
CI 3,187; 11,271), which implies that the risk of presenting chronic
obstructive pulmonary disease in surgical patients the oxidative
enzymatic response after preconditioning being 5 times greater
than in those without a personal history of chronic obstructive
pulmonary disease with a margin of 3 to 11 times.
In 1986, Murry CE et al. 12. described the concept of ischemic
preconditioning (PI) in dogs and since then it has been evaluated in
multiple animal and human models.
PI (development of tolerance to acute ischemia) is a cellular
mechanism capable of delaying, but not preventing cell death; This
protection is transitory and lasts from 1 to 2 hours in anesthetized
animals. During a brief episode of ischemia, adenosine, bradykinin,
norepinephrine, and opioids that activate G receptors are released
locally, culminating in the opening of ATP-dependent potassium
channels. The signals leading to the opening of these channels are
not fully defined, but include activation of phosphatidylinositol-
3-kinases, protein kinase C, and mitogen-activated protein kinase
(MAPK). Multiple aging-related abnormalities at various levels of
this cascade were demonstrated in animal models [13]. A clinical
trial published in JAMA demonstrates a reduction in the incidence
of postoperative renal failure in patients receiving IP compared to
the control group (37.5 versus 52.5%) and a decrease in the need
for renal replacement therapy. However, no differences were found
in terms of mortality and adverse cerebral and cardiovascular
events (although they were not the primary objective of the trial)
[14]. Also, in 2015 two essays were published both in the New
England Journal of Medicine. These are the ERICCA14 trial and the
RIPHeart trial [15].
The ERICCA trial, multicentre on more than 1,000 patients,
showed no difference in the primary endpoint (death, stroke,
acute kidney failure or acute myocardial infarction). No differences
were found either in the subgroup analyzes or in the secondary
objectives (troponin values, length of stay in the Intensive Care Unit
and mechanical ventilation, incidence of delirium and new atrial
fibrillation). No adverse effects were observed in the intervention
group [16] In the RIP Heart multicenter trial of more than 1,600
patients, no differences were found in the primary endpoint
(death, acute myocardial infarction, need for revascularization or
stroke), nor in the secondary endpoints (troponin elevation, acute
kidney failure, need for inotropes, length of stay in the Intensive
Care Unit and quality of life after the procedure). But, although
PI seems to have beneficial effects, what role does it play in the
case of elderly elective surgical patients in the local context? The
enzymatic response obtained was oxidative in most of the elderly
patients, which corresponds to 90%, showing no benefit. In a
2007 myocardial revascularization surgery study, 57 patients were
randomized to receive or not receive remote ischemia-reperfusion
cycles after anesthetic induction. The results showed a reduction
in troponin levels at 72 hours in the treated group compared to
the control group. Other trials confirm the cardioprotective effect
reflected in reductions in postoperative troponin T, I or CKMB
values. However, not all trials were positive in this regard and do not
confirm these results. The routine uses of inhalational anesthetics
or beta-blockers, which demonstrated their cardioprotective effect
in several clinical trials, is very likely to mask the beneficial effects
of PI. In any case, in a subsequent meta-analysis carried out by
d’Ascenzo et al. A decrease in troponin values was observed in
the postoperative period once possible confounding factors were
controlled, such as the use of such volatile anesthetics during surgery
[17]. Studies on IP, of different quality and with different objectives,
conclude similarly in IP, offering benefits in terms of decreasing the
values of markers for myocardial injury and incidence of kidney
damage in the immediate postoperative period, but it does not
seem to improve the short and medium term results when survival
and cardiovascular and cerebral adverse effects are analyzed. On
the other hand, cardioprotective drugs routinely used as inhalation
anesthetics, beta-blockers, and anti-calcium are sufficient, without
remote ischemia providing additional benefits. It is also not clear
which group of patients benefits from the technique, what is the
most appropriate method to perform it, and even whether or not it
has no adverse effects.
Conclusion
Research suggests that the mechanism of ischemic preconditioning is diminished in elderly patients, confirming essential arterial hypertension, diabetes mellitus, age, heart failure, cerebrovascular disease, chronic kidney disease, chronic obstructive pulmonary disease as independent cardiovascular risk factors in cancer patients.
Acknowledgement
Zaily Fuentes Díaz: review, analysis and bibliographical
selection; statistical processing; preparation of the final report;
review and correction of the report; review and final approval.
Gonzalo Fabián Orga García: field or assistance work; bibliographic
review, analysis and selection; survey application, statistical
processing; preparation of the final report; review and correction
of the report; review and final approval. Orlando Rodríguez Salazar:
review and correction of the report; review and final approval.
Jorge Lozano Casanova: sample processing and final approval.
Tania Puerto Pérez: statistical processing; review and correction of
the report and final approval.
Conflict of interest
The authors declare that does not exist an interest conflict.
Read More About Lupine Publishers Journal of Anesthesia & Pain Medicine Please Click on Below Link:
https://lupine-publishers-anesthesia-pain.blogspot.com/