Lupine Publishers| Journal of Textile and Fashion Designing
Abstract
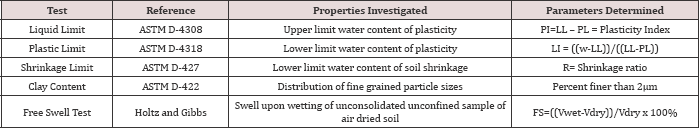
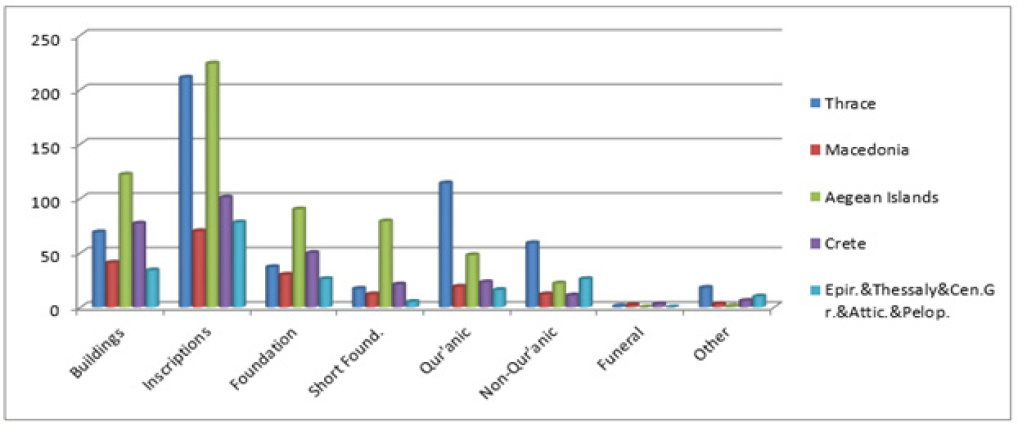
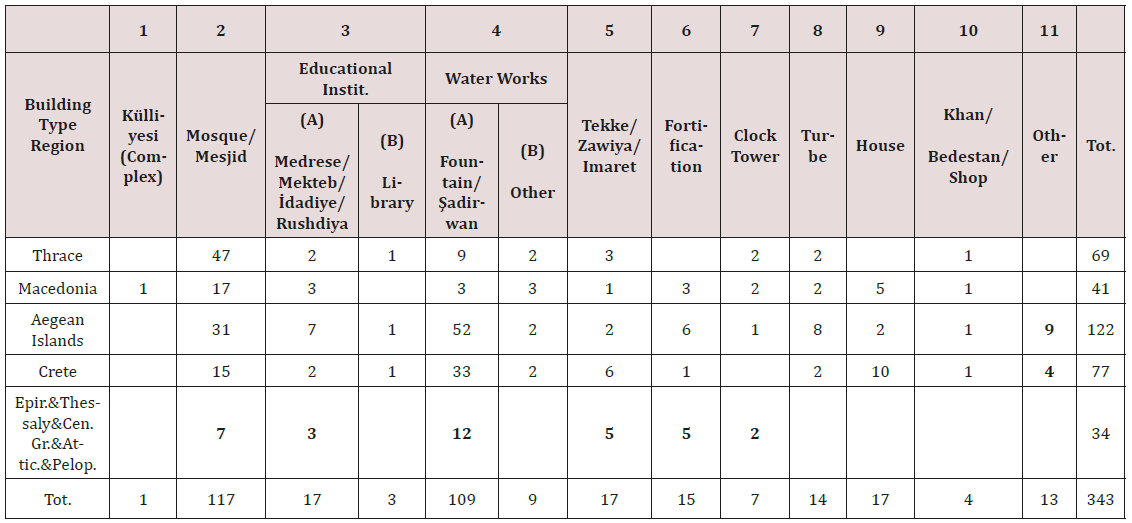
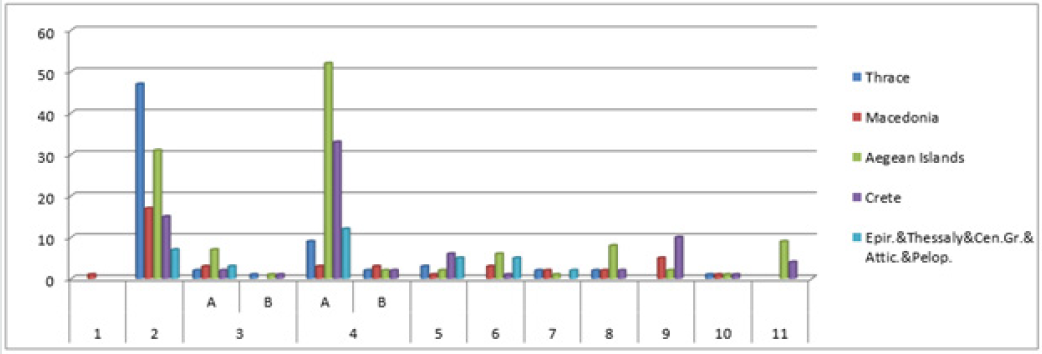
The treasure of Major natural fibres belongs to cotton, jute, wool, silk, flax, sisal and Manila hemp which are extensively used across the globe. Besides, a large number of fibres grown in lesser quantities throughout the world have local economic importance and are consumed locally. Utilization of underexploited, unexplored natural fibres from crop waste are not only critical issues in the international scenario but are also the need of the hour in developing countries like India to search out a suitable avenue for which separate spinning system is not widely available or established. Pine apple leaf fibre successfully tested as a base material for conveyor belts in the early eighties, could well have been the magic yarn of the day. Pineapple leaf fibre extracted from the green pineapple leaf, an agro waste reveals its immense potentiality in the field of textiles particularly due to the disposal problem after harvesting for cleaner and green environment.
PALF is well known for its silky lustre which possesses some advantageous physical and chemical properties like high tensile strength, dimensional stability, considerable resistance to heat and fire, and good dyeability while the demerits are coarseness, inextensibility. Besides, it is a low cost renewable resource and eco-friendly material. If the apparent demerits can be masked, a diverse range of products can be developed by exploiting the intrinsic properties of PALF. One of the ways of masking is blending of PALF with natural and synthetic fibres. It is felt that such binary blending will help development of textiles with better functional properties by combining positive features of the constituent fibres. Therefore, binary blending will give a wider application for production of value added diversified products which are the need of the hour.
The paper also delineates suitable processing technique for blending of PALF with different natural and synthetic fibres for conversion into textiles using existing fibre processing system since there is no specialized spinning system available for pineapple and their possible commercial utilization. The PALF blended yarn has a bright future prospect for sustainable luxury textiles like fancy apparel products (Figure 1).

Introduction
Wealth from waste is no more a slogan in 21st century but achieved successfully turning pineapple leaves into wealth which not only creates green environmental sense but also turns waste into wealth. Resource depletion and global warming have driven each industry to move toward a greener and sustainable industry. Lignocelluloses, the most abundant renewable biomass is composed of cellulose, hemicelluloses and lignin, as well as other minor components. Pine apple leaf fibre successfully tested as a base material for textiles in the early eighties, could well have been the magic yarn of the day. Research work on pineapple leaf fibre, an agro waste reveals its immense potentiality in the field textiles particularly technical textiles. Sufficient fibre will be available to arouse interest if the fibre is extracted commercially. Due to non-availability of specialized spinning system for PALF in India, it will be much easier to promote PALF in any of the existing spinning systems provided an appropriate processing technology is developed.
Major natural fibres belongs to cotton, jute, wool, silk, flax, sisal and Manila hemp which are extensively used across the globe possess suitable processing technology and developed machinery. Besides, a large number of fibres grown in lesser quantities throughout the world have local economic importance and are consumed locally The pineapple plant AnanasComosus (L) is a member of the family Bromaliaceae of the monocotyledonous, containing 1,300 species; most of which are native to tropical America. Although over nearly 90 varieties of the plants cultivated in various parts of the world, only 3 varieties, namely, Kew, Queen and Mauritius are cultivated commercially. The form of pineapple leaves varies and depends on the position of the stem and age.
According to the data available, Pineapple fibre can be profitably produced in Tripura as well as Siliguri in West Bengal, where extensive pineapple farming takes place. In India, Pineapple leaves are never cut off, and are cleared when the plants naturally shed them. As a result, fewer pineapple plants are grown in India, as the leaves cover a lot of space. In countries like Brazil where extensive pineapple farming is done the leaves are cut away to make space for more plants. "We have gone through the science of it- Interestingly, cutting away of the leaves does not harm the plant and in fact helps it grow bigger fruit, as the leaves normally draw away a lot of the nourishment” says Dr. S. K. Dey, Senior Scientist of ICAR-CIRCOT, Mumbai. Indian farmers mostly throw away the leaves. Research on plantation has established that the leaves can be cut three times a year, without harming the harvest and suitably designed industry for pineapple leaf fibre, can run the year-round on these supplies.
The philosophy of blending between two fibres depends on two basic principles which apparently appear to be a bit contradictory.
a) PALF may be blended with cheaper fibres so that a cheaper product mix becomes feasible. In this category, blending of ramie with jute, ramies, Mesta, banana, Roselle hemp appear to be worth pursuing.
b) PALF is often blended with synthetic fibres to produce diversified blended fabrics which are expected to fetch higher prices per unit weight of ramie and consequently higher profitability.
PALF is well known for its silky lustre which possesses some advantageous physical and chemical properties like high tensile strength, dimensional stability, considerable resistance to heat and fire, and good dyeability while the demerits are coarseness, inextensibility. Besides, it is a low cost renewable resource and eco- friendly material.
Normally, the fibre is as fine as the finer quality jute, although about ten times as coarse as cotton. Unlike jute, its structure is without mesh, filaments are well separated and it is two and a half times more extensible with superior bundle strength and L/B ratio. Both the flexural and torsional rigidity of pineapple leaf fibres are comparable with jute fibres of less rigid quality. An interesting characteristic was observed in the case of pineapple leaf fibre and yarn when their tensile properties were studied in wet condition. The bundle strength of pineapple leaf fibre decreases by 50% when in a wet condition but the yarn strength increases by about 13%. A detailed research reveals that the frictional property of pineapple leaf fibre is very high in the wet condition and it predominates over the fall in tensile strength of the fibre so as to increase the wet strength of the yarn.
Different Stages of Blending Process
The development of blended yarn from PALF with natural and synthetic fibres can be achieved in the three stages of processing as given below.
a) Blending at carding or drawing.
b) Blending at spinning
c) Union blending i.e. at fabric stage.
Blending at Carding or Drawing
I. Jute Spinning System: The processing technology of pineapple leaf fibre in jute, cotton, semi-worsted and flax systems as well as to compare performance, research work was undertaken at Jute Technological Research laboratories which later on renamed as National Institute of Research on Jute and Allied Fibre Technology, Kolkata.
II. Performance of jute/Pineapple Leaf Fibre on Jute Spinning System: When the golden fibre blends with pineapple, a magic yarn is born. The fibre is best used as decorative material. Firstly, the natural colour is creamy white-hence unlike jute it does not need bleaching. We have tried various combinations of the fibre at our pilot plant and blended it with jute and synthetic material. When blended with synthetic material, the product is an extra fine material. It can work wonders with jute. If pineapple fibre is blended with jute up to 20-25% fine yarn of linear density of 69 tex or less can be created. This is very difficult to achieve with Indian jute alone.
III. PALF-Ramie Blended Yarn: PALF and ramie yarns spun in dry and wet spinning systems are comparable but wet spun yarns reveal better performance than dry spun yarns due to better inter fibre friction in the wet spinning system. By gradual increase in the percentage of PALF in the blend, a gradual decrease in tenacity of the blended yarn has been observed. And this may be due to the difference of fineness of the two fibres.
IV. PALF-Viscose Blended Yarn: 100% viscose yarn spun in jute spinning system shows higher tenacity for wet spinning and lower extension compared to dry spinning. Gradual increase of PALF in the blend brings about gradual improvement in the tenacity of the blended yarns due to higher strength of PALF. The wet spun blended yarn from PALF-viscose show better performance than corresponding blended yarns spun on the dry spinning system.
V. PALF-Polypropylene Blended Yarn: Binary blending of PALF -Polypropylene for its use in sophisticated area of textiles, Polypropylene fibre of 15 denier and 120 mm length was used. Both PALF and Polypropylene fibres were processed separately in Flax Finisher card with the developed technology of processing the above fibres and a linear density of 138 tex was spun with 5.5 T.P.I in both dry and wet spinning system. Binary blending of the carded material was achieved at Mackie's First Screw Gill Drawing frame with a blend proportion of 75:25, 50:50 and 25:75. No difficulty was encountered during spinning of blended yarn and control yarn.
VI. PALF-Acrylic Blended Yarn: PALF: Acrylic: 50:50 blended yarns having linear density of 84 tex with a T.P.I of 7.5 were developed in jute spinning system in dry and wet spinning conditions. Four blended yarns were spun by blending PALF and acrylic at four different stages of Jute processing viz, carding and three drawing frames. The performance of the blended yarns was studied to evaluate the optimum stage of mechanical processing for binary blending of PALF and acrylic.
Wet Spinning Technology
Wet spinning brings about improvement in short-term weigh irregularity of the yarns resulting in better regularity of yarn diameter. This is chiefly due to better control of fibres in the drafting zone of the spinning frame during wet spinning. The diameter of wet spun PALF yarn of equivalent linear density is lower and its packing coefficient is also higher than that of the dry spun one. The tenacity of the wet spun yarn is higher than that of the dry spun one as the regularity of wet spun yarn is better and the higher packing coefficient is expected to generate transverse pressure during tensile loading. The strength C.V % of wet spun yarn was also lower compared to dry spun yarns. There was no significant difference in breaking elongation of dry and wet spun yarns.
Short staple Cotton Spinning System
Pineapple leaf fibre was first stapled to 32 mm, opened in a single opener machine, blended with Indian cotton in two proportions
A. 67% cotton: 33% Pineapple leaf fibre
B. 80% cotton: 20% pineapple leaf fibre and yarn of a coarse count 14s spun. The performance of the blended yarns showed that on increasing the proportion of pineapple leaf fibre in the blend, the count strength product and regularity deteriorated and a higher percentage of droppings of fibre was noticed in the blow room and carding machine. Spinnability of PALF improves after chemical treatment which was not achieved from cotton/raw PALF (67:33) blend composition. It is clear that the Spinnability increased from 14s to 22s with higher blend composition of PALF: Cotton:: 70:30. Yarn performance indicates that the C.S.P of the blended yarn is lower compared to cotton yarn. The cohesiveness of chemically treated PALF needed higher twist multiplier than normal cotton yarn of same count.
Semi-Worsted Spinning Systems
PALF were blended with Chokla variety of coarse Indian Wool at Central Sheep and Wool Research Institute, Avikanagar, Rajasthan, a sister concern of Indian Council of Agricultural Research. Yarns of nominal linear density of 138 tex were spun on the semi-worsted spinning system by varying the blend proportion of PALFs. Blending of PALFs by 25% could bring about a sharp drop in breaking elongation of yarns and blending by 50% results a sharp increase in tenacity of blended yarns. Besides, by blending PALF with wool at 25:75,the bulk resilience of yarn decreased only by 10% as compared to all wool yarn. The blended materials of PALF-Wool, all PALF and all wool were processed separately on the semi worsted spinning systems.
Eri Silk Spinning Systems
Latest finding reveal that pineapple leaf fibre was successfully processed and blended with red eri available in north eastern region only using Chinese silk processing facilities available at Fabric Plus, Guwahati. Red eri and softened pineapple leaf fibre were processed through the sequence as follows:
Floss Cutter - First Circular Dressing - Second Circular Dressing - Third Circular Dressing - First Spreader - Second Spreader - Slivering - First Drawing-Second drawing - Third Drawing- Roving - Ring spinning - Winding - Twisting - Conditioning - Singeing - Package.
Finer linear density of PALF: Red Eri blended yarn reveals its immense potentiality to be used in the field of Luxury textiles. Finest blended yarn could not be spun except this spinning system. The mechanical properties of the blended yarn were up to textile quality.
Conclusion
Investigation on pineapple leaf fibre clearly indicates that the agro waste can be suitably processed into useful products. Development of appropriate processing technologies for generating yarn with improved properties can widen the application ofthis agro waste.The extractor can effectively be used to extract the fibre from the agro waste of pineapple leaves and the residual sludge obtained after scratching the leaves can be used for vermicomposting successfully. Investigation on pineapple leaf fibre clearly indicates that the agro waste can be suitably processed into useful products. Development of appropriate processing technologies for generating yarn with improved properties can widen the application of this agro waste. The integrated technology for the extraction of pineapple leaf fibre and the vermicomposting altogether becomes remunerative to pineapple cultivators which can be adopted by all pineapple growers not only for additional income but also proper utilization of wastes particularly agricultural wastes which is an important factor in planning the economic progress of a developing country like India.
Read More About Lupine Publishers Journal of Textile and Fashion Designing Please Click on Below Link: https://fashion-technology-lupine-publishers.blogspot.com